Netwrix Auditor is a security solution that helps organizations overcome compliance and operational challenges. Netwrix...
Software Advice offers objective, independent research and verified user reviews. We may earn a referral fee when you visit a vendor through our links.
Learn more
Our commitment
Independent research methodology
Software Advice’s researchers use a mix of verified reviews, independent research and objective methodologies to bring you selection and ranking information you can trust. While we may earn a referral fee when you visit a provider through our links or speak to an advisor, this has no influence on our research or methodology.
How Software Advice verifies reviews
Software Advice carefully verified over 2.5 million+ reviews to bring you authentic software and services experiences from real users. Our human moderators verify that reviewers are real people and that reviews are authentic. They use leading tech to analyze text quality and to detect plagiarism and generative AI.
How Software Advice ensures transparency
Software Advice lists all providers across its website—not just those that pay us—so that users can make informed purchase decisions. Software Advice is free for users. Software and service providers pay us for sponsored profiles to receive web traffic and sales opportunities. Sponsored profiles include a link-out icon that takes users to the provider’s website.

Blue Lava
About Blue Lava
Blue Lava is a SaaS platform, designed with, by, and for CISOs, that offers a holistic solution for security professionals to manage security programs. CISOs can take a control framework-focused approach or a risk-focused approach to assessing the current state and maturity of the organization or individual areas of the organization.
With copy and clone features, Blue Lava provides a consistent method for repeating assessments year over year, quarter over quarter, or at any cadence. Likewise, as subject matter experts update responses, they can also provide links to updated evidence as verification. Blue Lava does not directly capture evidential artifacts but rather captures only contextual attributes such as the name, owner, link and expiration dates for the evidence. This gives CISOs full security and access control permissions over the original content and allows the subject matter experts the ability to quickly and easily provide proof of their responses for each assessment.
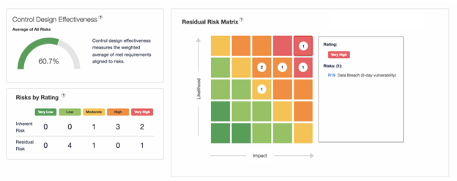
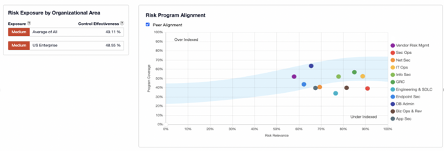
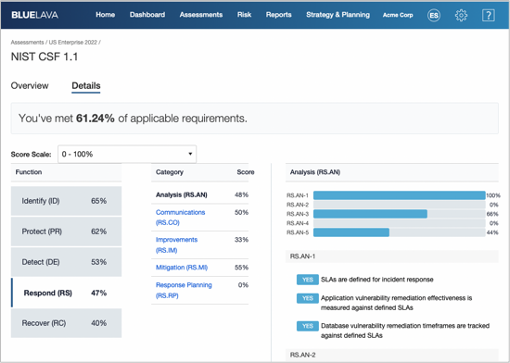
Once the security team has baselined the program with requirements and risk information, Blue Lava supports the triage and management of gaps and deficiencies identified from the baseline assessment. Blue Lava automatically creates findings from any unmet requirement, populates recommendations for closure, and provides pre-templated views to review and assign findings for remediation or risk acceptance. This includes out-of-the-box themed views to rank and order the resulting findings by maturity, by common themes, or prioritized by risk.
During this triage process, Blue Lava natively supports simulation functionality to group findings into different scenarios for remediation or risk acceptance. Using this functionality CISOs can prioritize individuals or groups of findings to be placed into projects for management and remediation. The simulations functionality reviews priority and any provided resource needs for people, technology, and time to remediate the associated findings. The simulations engine then calculates the potential NIST coverage scores and BL CMM maturity levels that would be achieved if all findings were remediated. This allows CISOs to predict which projects would be best to fund to achieve an increase in NIST score, and maturity or to optimize limited resources across different potential projects.
As Findings are prioritized and marked for remediation, CISOs can leverage integrations to existing ticketing tools, such as Jira Cloud, to bidirectionally manage the workflow of the finding through closure and remediation. This allows organizations to maintain the existing process and communication channels for managing gaps and issues without having to log into separate tools or manage multiple workflow processes. Once findings are aggregated into projects, using the simulations algorithm to create different project scenarios or using the different pre-populated themed views, security program owners can assign ownership and add resourcing and staffing information to projects for remediation. These tactical projects natively can roll into higher-level strategic action plans that make up the goals and Initiatives for the security program. CISOs can, therefore, directly identify, document, track, manage, and report on their objectives and key results (OKRs) and strategic goals and initiatives for the program using the Blue Lava platform.
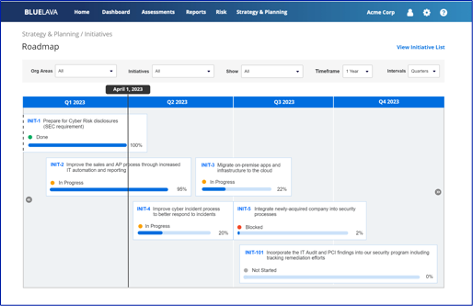
Natively the progress, status, and percent complete for each of these initiatives can be dynamically viewed, managed, and presented using the Blue Lava roadmaps functionality. This presentation-ready visualization allows CISOs to dynamically select different areas of the business, key initiatives, and attributes of that initiative to share with various stakeholders.





Blue Lava pricing
Starting Price:
Not provided by vendor
Show more details
Free Version:
No
Free trial:
No








